Enterprise Resource Planning

Fully Customizable
Implement the workflows as per your requirements and define approval trees.
Scalable
Adapts and grows seamlessly with your business needs, expanding its capacity and performance as demands increase.

Secure
We implements robust security measures to safeguard sensitive data, utilizing encryption, authentication, and access controls.
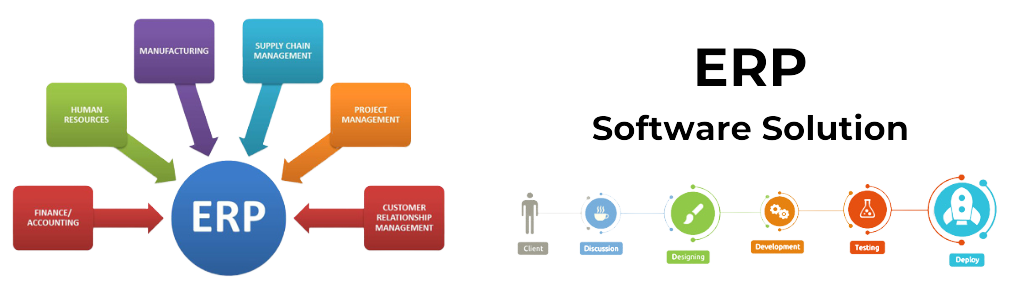
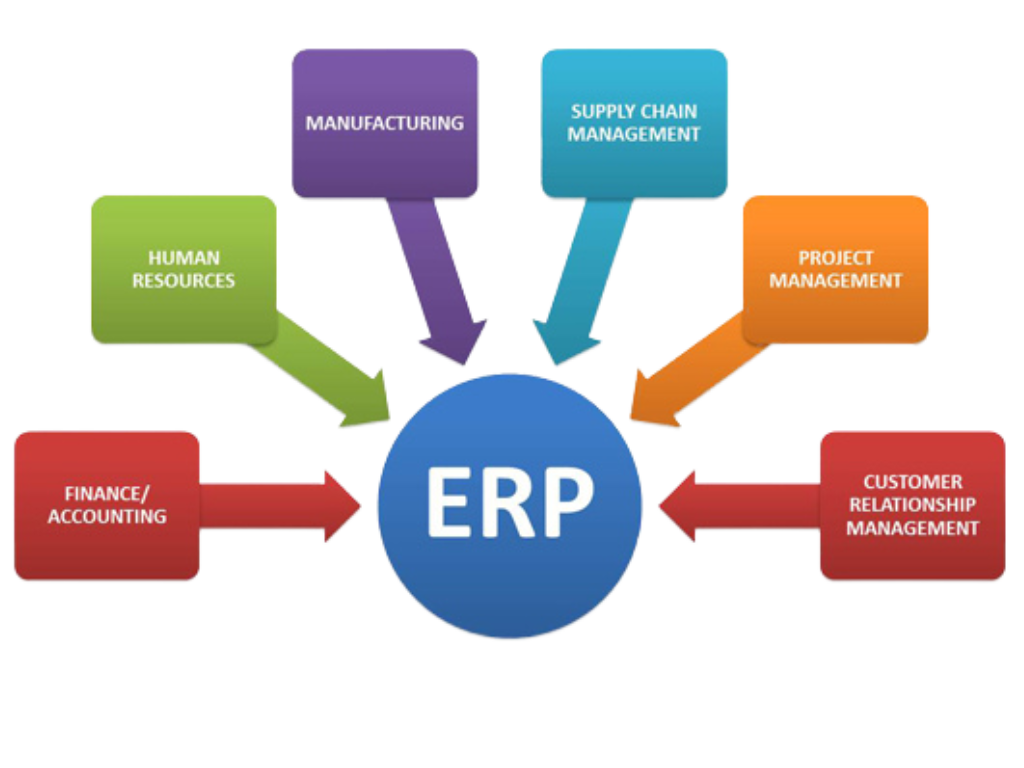
Our Modules
What Customers Say About Us
Even the all-powerful Pointing has no control about the blind texts it is an almost unorthographic life One day however a small line of blind text by the name of Lorem Ipsum decided to leave for the far World of Grammar. The Big Oxmox advised her
Shams W.Pawel
Founder & CEO of XpeedStudio











